Tuning Into the Hacker Mindset: OSINT Video Agents, Man-In-The-Malware, Flipper Zero Recon, and Social Engineering - Lessons from DEFCON33
Real-world lessons from DEFCON33 on how hackers use tools, tricks, and mindset to peel away the abstractions of systems
When I was 12 years old, I jailbroke my iPod touch running iOS 3.1.1 with BlackRa1n, downloaded Cydia, and opened myself to the world of sidechaining software on devices. I remembered the thrill of watching an iPod come alive after a jailbreak — suddenly a locked device felt like a sandbox. Fast forward to DEFCON: the same electric curiosity is still there, but the toys have changed. In August, I galloped from Ham operators at the Toxic BBQ, to Flipper Zero exploits, to conducting video agents using OSINT, to vishing competitions that sounded like theatre and fieldcraft at once. This post is a day-by-day guided tour of what I saw at DEFCON33, from Wednesday, 8/7 to Saturday, 8/10.
Going into DEFCON, I heard lore on the social engineering village, knew a bit about the Flipper Zero, and played around with Wireshark before while at Berkeley. However, after attending DEFCON, my mind was opened to the world of security.
For security researchers operating ethically, and disclosing security bugs to corporations, in this case, Apple “find my” exploits, there is a long winded process for them to recognize and even acknowledge that there is a bug, yet alone getting paid for your work. If you can’t show convince the company of the detrimental impact of your exploit, then they will try to downplay the severity and payout.
Flipper Zero’s are one of the most versatile devices to exploring the wireless world around us. Master the tool to master the airwaves.
The Phrack Magazine spearheaded some of the key cornerstone members of the community. Phrack published, malloc des-maleficarum, which generalized arbitrary code execution through heap overflows, and where CTS got into hacking. The written word unlocks the depth of the community.
Get doors to open with the pretext of a position of authority. When witnessing the social engineering village, the contestants that came with it with a simple and clear pretext, calling on behalf of Corporate Rite Aid Security or a private equity audit department, were able to get the other side to disclose information rather easily.
Toxic BBQ is a great place to co-mingle and chat with the hacking community. I heard stories of people using the flipper zero to clone friend’s garage door to save his friend from walking down 4 sets of stairs, to Flipper Zero’s prowess in disconnecting power plants from the German energy grid, to analyze train frequencies and send CONNECT and DISCONNECT signals.
Table of Contents:
Four Most Eye-Opening DEFCON Talks
Tactical Flipper Zero: You Have 1 Hour and No Other Equipment by Grey Fox
SEC Vishing Competition by the Social Engineering Village
Autonomous Video Hunter: AI Agents for Real-Time OSINT by Kevin Dela Rosa
40 Years Of Phrack: Hacking, Zines & Digital Dissent with richinseattle, Netspooky, Chompie, cts, and Adam 'pi3' Zabrocki
8/7/2025 (Wednesday)
8/8/2025 (Thursday)
Hak5 (WifiPineapple Pager) and the Red Team Tools booth
AI Village with Reality Defender
Wall of Sheep by the Packet Hacking Village
Hacker Jeopardy
8/9/2025 (Friday)
nRootTag - Exploiting Find My and Transforming Computers Into Unauthorized Trackers by Chapoly1305
Meshtastic Under the Microscope: From Chirps to Chat by Allan Riordan Boll
Compromising Threat Actor Communications
Level UP OSINT by Mishaal Khan
Maritime Hacking village
Anatomy of a Crypto Scam by Nick “c7five” Percoco and Kitboga
8/10/2025 (Saturday)
Portswigger Awards: Top 10 web hacking techniques of 2024
Four Most Eye-Opening DEFCON Talks
1. Tactical Flipper Zero: You Have 1 Hour and No Other Equipment by Grey Fox
This was by far the best talk I saw at DEFCON. Grey Fox comes from 20 years in the air force, has a background in signals and digital network intelligence, and is now an RF and wireless tech educator.
The Flipper Zero is a Swiss army knife for conducting chemistry with wireless signals. It has built in radio chains for BLE (Bluetooth Low Energy), sub-GHz, NFC (Near field communication), RFID (Radio Frequency Identification), IR (infrared) and iButton.
The goal for the talk was to speedrun survelliance on a high value individual (HVI), which just a Flipper zero, an ESP32 submodule to half-duplex (transmit and receive on different frequencies), and an external sub gigahertz antenna (useful for picking up radio signals, IoT signals, Car Fobs, TPMS (Tire Pressure Monitoring System), everything that operates below 1 GHz)
Let’s see what it can do.
Note: with this toolkit, information and mastery of the Flipper Zero, it’s possible to rig the roulette table to always return red, ALL-IN on red, then cash out. Don’t be a criminal.
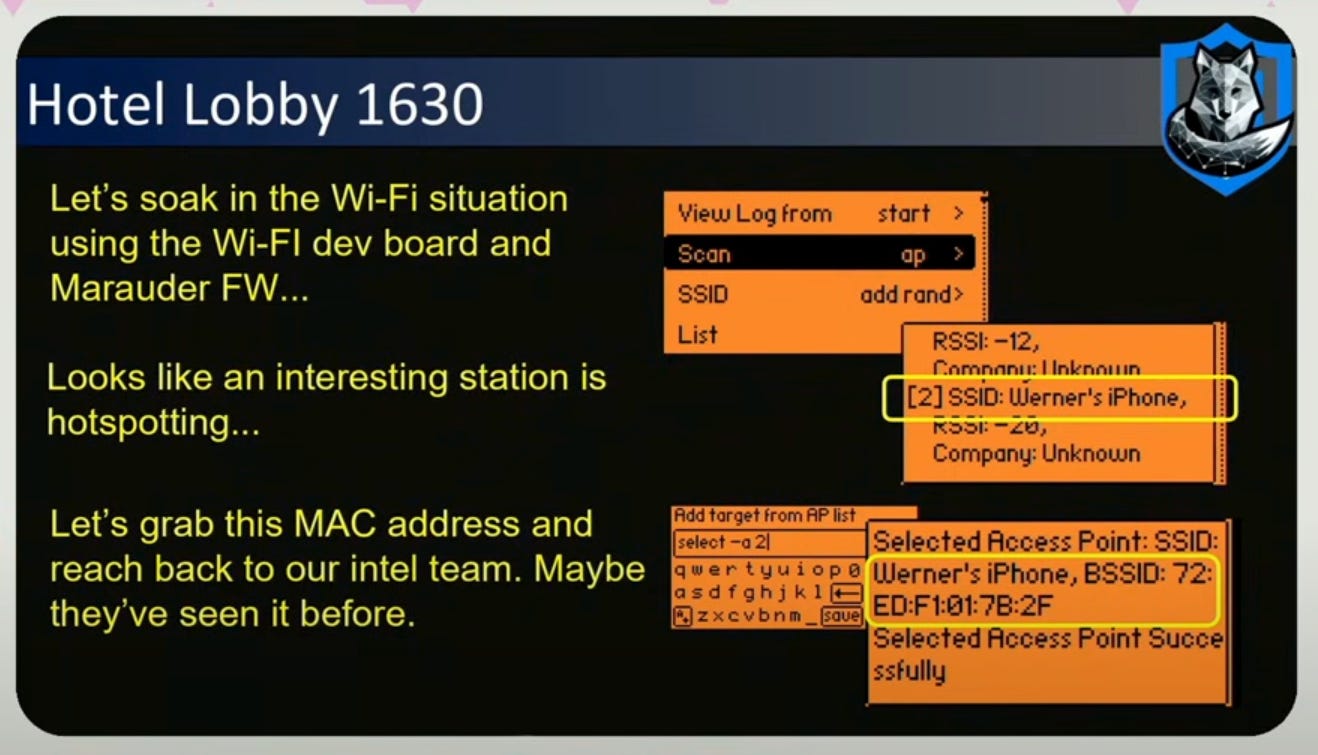
First thing to do is add a WiFi dev board and scan the surroundings, to try to figure out the MAC address of the HVI’s phone, since this is meant to be a unique identifier.
The way this works is that from a user experience and quality of service aspect, when your phone has wifi on and is not associated with a wireless network, your phone is going to be beaconing out to all the networks you ever joined. So everywhere you go, you are blasting out wifi beacons.
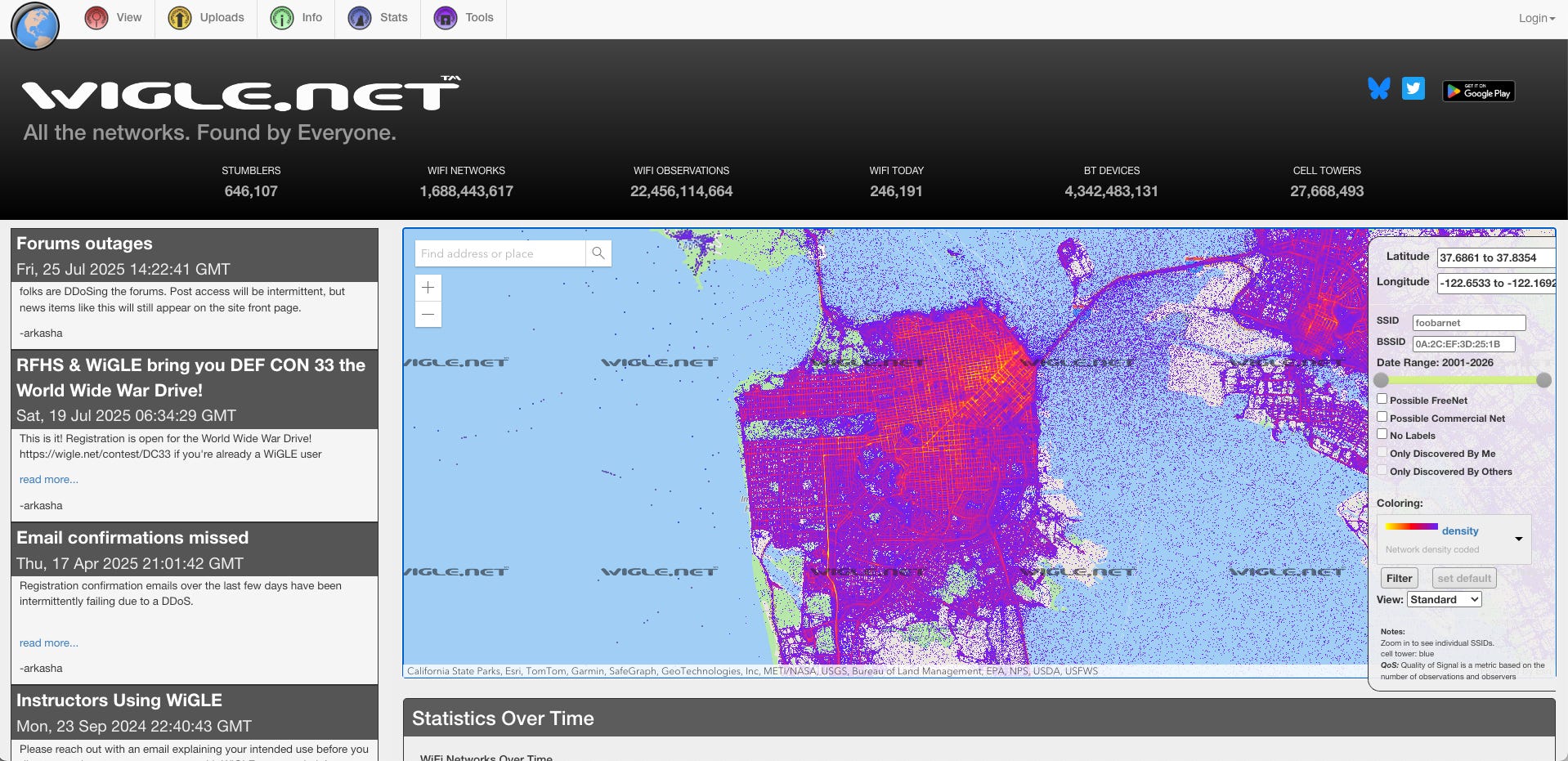
Using wigle.net, we can see an open list of WiFi networks out there in the world, and with knowing the list of networks that the High Value Individual (HVI) has connected to before, we could spoof an existing WiFI network based on the geolocation.
Montgomery and 2nd street, “are you my Wifi”?
Dolores Park, “are you my WiFi”?
Salesforce tower, “are you my Wifi”?
Collect these, and then create a pattern of the locations that HVI is visiting.
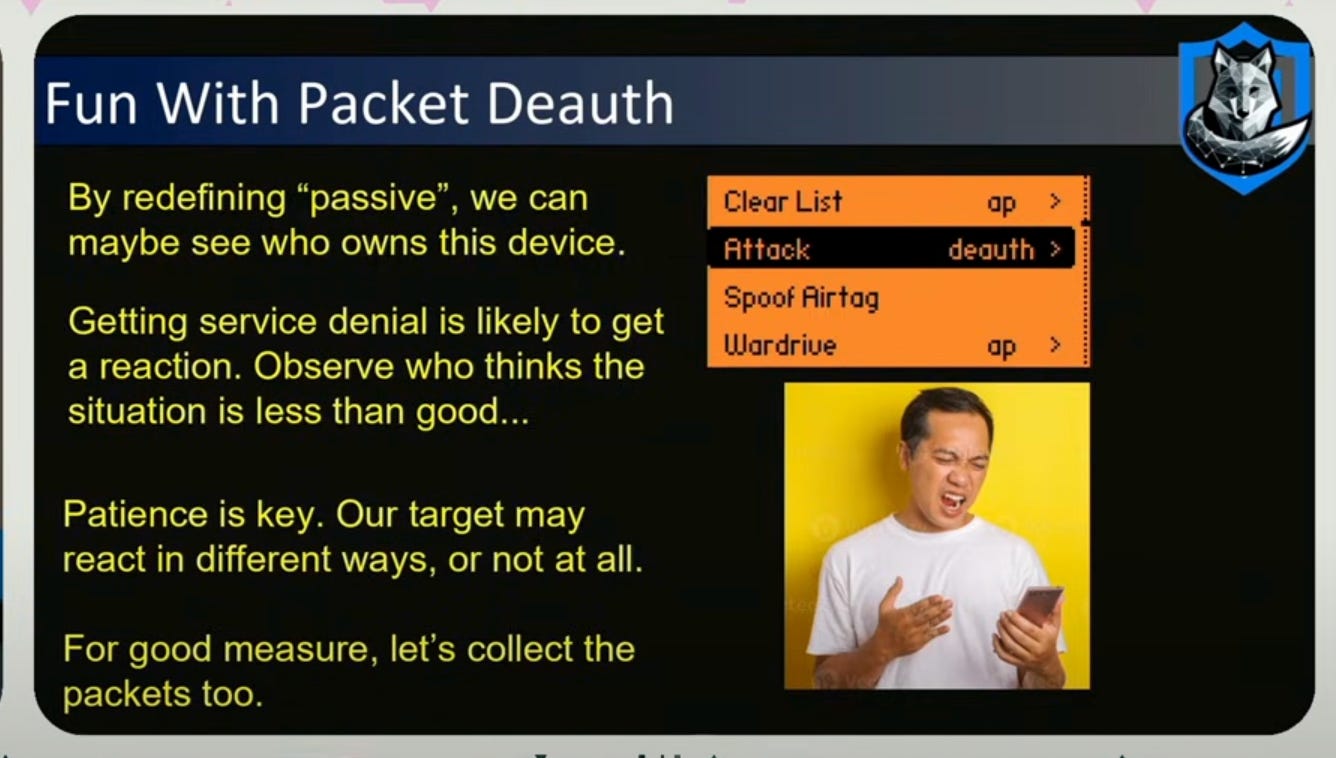
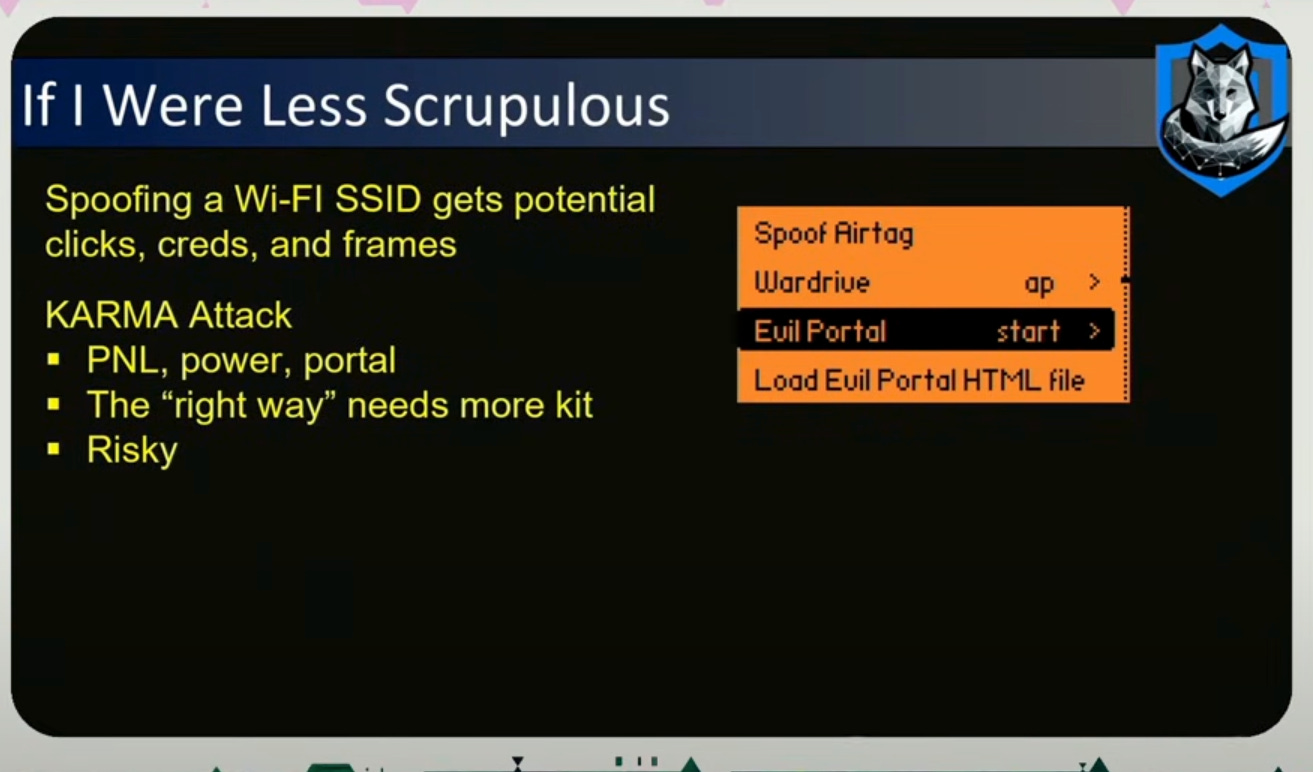
Another approach to do this is to run a KARMA attack and spoof an existing network.
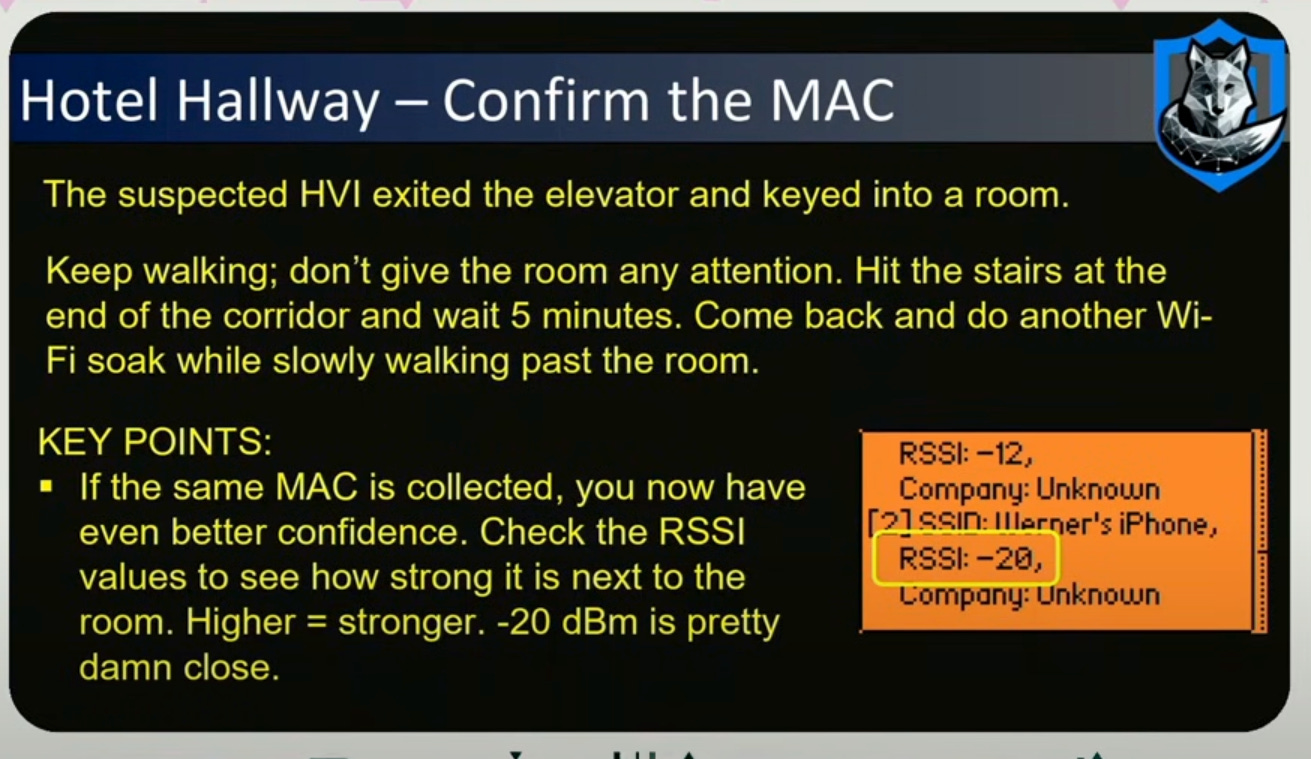
If the suspected HVI goes into a hotel room and you hypothesize you have the MAC address, then as you tail them into their hotel lobby, you can check the RSSI values to see how close their wifi signal is. Higher = stronger. -20 RSSI is pretty good signal that you uniquely identified their device with a MAC address.
After collecting the MAC addresses, you can setup a SIGINT trip wire. With an ESP32 chip putting out 2.4 GHz, you can program it to detect a whitelist of MAC addresses and you can put that anywhere, as leave behinds for a route, and if that WiFi or mac address is detected, it will alert you which is akin to near real time tracking.
The Flipper Zero also has the ability to read credit cards. Imagine the HVI is sitting at the 1 Hotel, drinking a cappuccino, enjoying the beautiful California sunshine on their skin, when they leave to go to the bathroom, leaving their wallet, keys on the table outside. We can swoop in, and read the credit card with conduct an NFC read with the Flipper Zero.
This is really good for ubiquitous technical surveillance because then we have unique identifiers that we can match up against national collections or even breach data as a civilian, and that breach data will tell me where the credit card was used, purchases were made, online stores where information was saved.
Flipper Zero also has a great signal replay - let’s clone the HVI car’s signal.
There are two routes to take, cloning the lock or unlock signal. For our mission, we clone the lock signal, because we wanted it to be a clandestine action.
Clandestine actions are actions done secretly so people don’t know, while covert actions are done so everyone knows. Since our goal was to indicate the vehicle and not get into the vehicle, we clone the lock signal.
The reason why we want to copy the lock signal is that because of how remote entry was designed even for older cars from the 2000s, anytime you tried to unlock the vehicle, the onboard system will sequentially go up to the next code, and to the next code and next code, and as long as it was aligned with the key fob, you would be able to unlock it on the first try.
With older vehicles, you are able to copy a signal from the Flipper Zero without the vehicle being in the vicinity so that the vehicle wouldn’t hear the signals. If we click unlock 5 times on the flipper zero, but then go back and try to use the key fob to unlock, it will take 5 tries clicking on the unlock button to align the onboard system with the key fob to get a proper unlock.
Remember when Yoda talks to Luke Skywalker?
“The force’s energy surrounds us and binds us. You must feel the force around you”
The Flipper Zero is the key to the force, enabling us to control the wireless spectrum around us, molding it, shaping it, and modulating it according to will.
Pick one up here and get a wifi devboard.
Full talk here:
Resources:
Ecosystem around the flipper zero
2. Autonomous Video Hunter: AI Agents for Real-Time OSINT by Kevin Dela Rosa
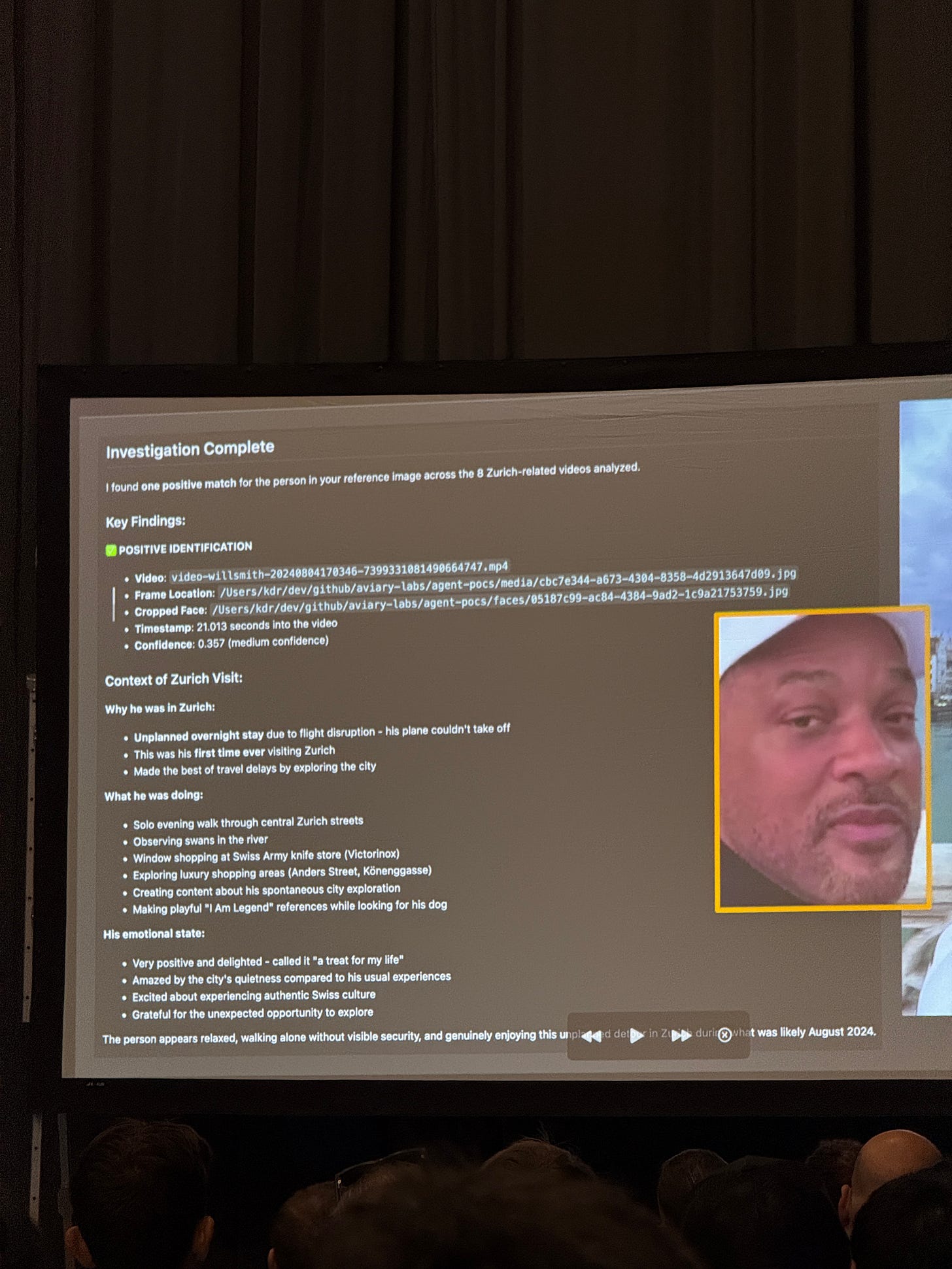
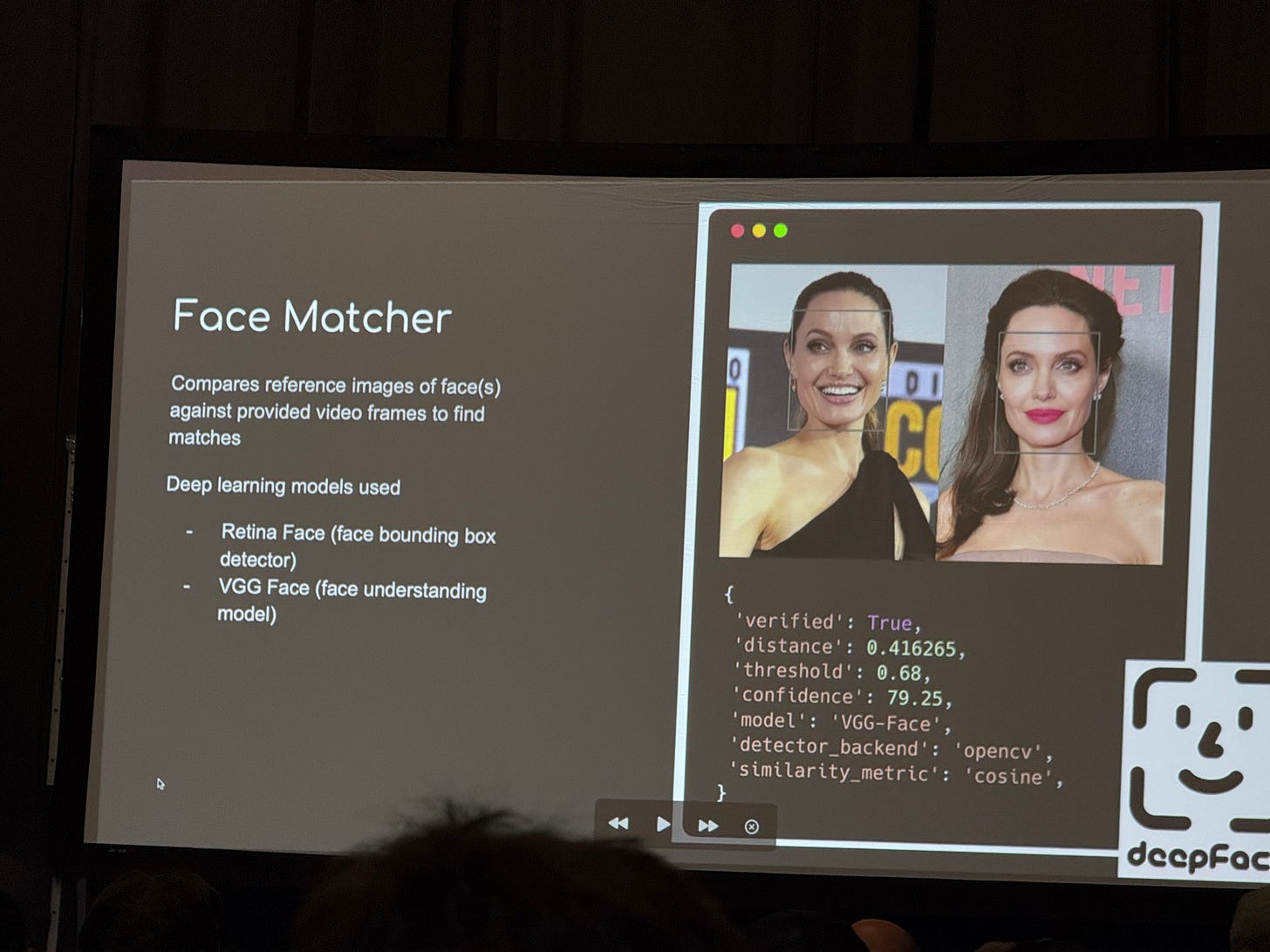
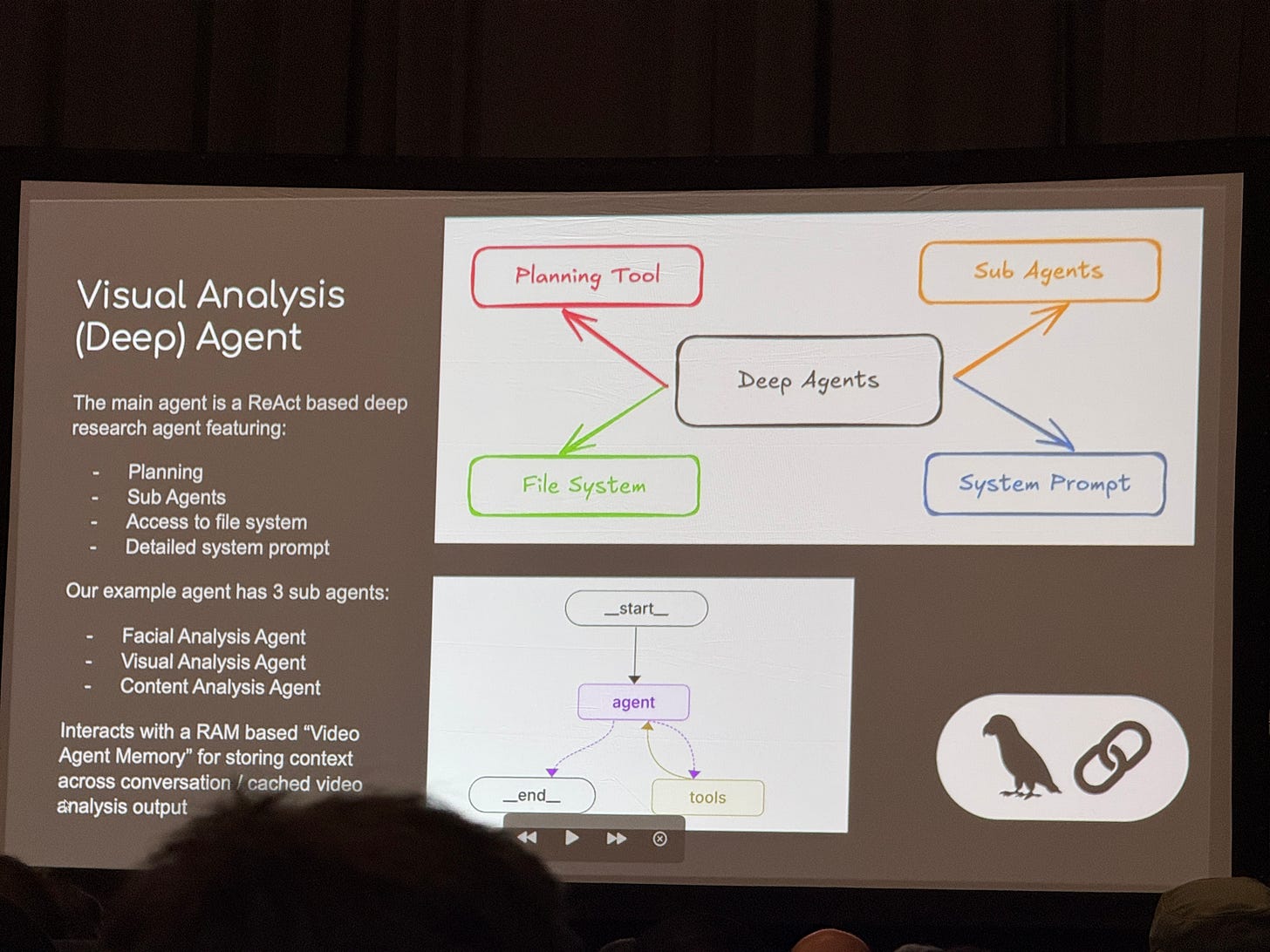
Autonomous Video Hunter (AVH) is a system of AI powered agents that scour video content in real time to extract actionable OSINT from them. The way this works is by chaining multi subagents together — a facial analysis agent, a visual analysis agent, and a content analysis agent, to extract domain specific information from a video.
Hosted by the Recon Village. Slides here:
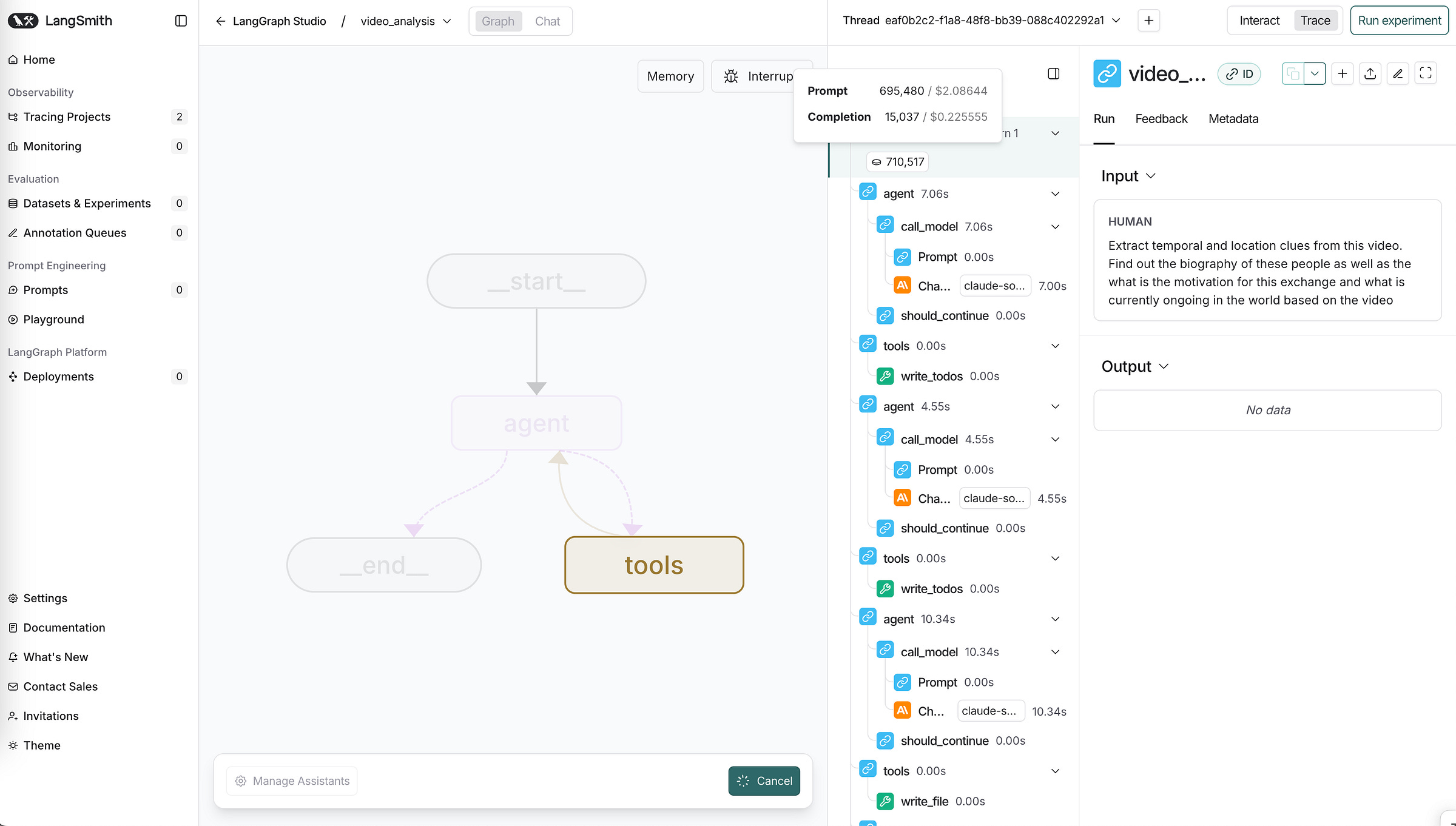
I ran the AVH agent myself locally and I was impressed with the level of detail and extraction from detecting the faces, to building out transcriptions from the video, however, it seemed like the number of tokens needed for processing a video was quite high. A 3 min video required a 695,000 tokens, which was still ongoing in Langsmith.
Run the Autonomous Video Hunter yourself from the repo here.
References:
3. SEC Vishing Competition by the social engineering village
One of the lores from DEFCON, I heard of a SE who was given the flag of getting the CEO of ExxonMobil on the phone - they got to their chief of staff on the phone, but with proper SE training, the chief of staff knew she was being targeted and terminated the call. Although the ultimate flag escaped the grasp, the skills, cunning, and nuance were a display in prowess of the english language and so I had to go here and see it for myself.
Word of note to future attendees:
This is one of the more hyped events at DEFCON and so there is easily a looong line out the door for this. My friends and I snagged a seat in the first two rows by getting here early and attending the Improv talk from SE earlier. Don’t show up late to this event, otherwise you will not see it!
There were two SE hackers that stood out from the pack here, Vishful Thinking and 0xf1sh.
A bit on the background of the competition - competitors are inside a phone booth mic-ed up so that all 200+ attendees in the audience can listen to the call. In order to obtain points in the CTF, they have to get their target to provide answers to questions like
What is the name of the company VPN?
Do they block websites?
If website block = yes, which ones? (Facebook, eBay, etc.)
Is wireless in use onsite? (yes/no)
To conduct this successfully, contestants adopt different pretexts in order to convince the person they are speaking on the phone.
Contestants are given a 15 min block where they call up different stores and employees to extract as much information as possible.
Vishful Thinking’s approach to calling Rite Aid’s stores and pretext it with, “I’m calling on behalf of Rite Aid Corporate, looking to cross off your store from my checklist given the merge that’s about to happen” was genius. (Rite aid is currently undergoing a Chapter 11 bankruptcy filed in May 2025, with the intention to sell virtually all of its assets to other companies)
By using the pretext of Rite Aid Corporate Security, she called from a position of authority and was able to successfully go down the flag checklist.
Another interesting observation is that when switching pretexts, social engineers also switch up the wardrobe and accessories. Calling on behalf of Rite Aid Corporate or a private equity associate, Vishful Thinking removed glasses, changed to a different outfit and even added a “store closing sign” to the window booth.
Another great contestant was 0xf1sh. They called CarMax and were able to get them to reveal information about their on premise security protocols and go down the flag checklist as well.
Thank you to the judges, Next Jenn and KnaveSec. For getting into Social Engineering, I would recommend watching The Basics of Social Engineering by Chris Pritchard from DEFCON.
References:
4. 40 Years Of Phrack: Hacking, Zines & Digital Dissent by richinseattle, Netspooky, Chompie, cts, and Adam 'pi3' Zabrocki
Phrack is one of the most well regarded hacking publications. Started on November 17th, 1985, Phrack takes its name from the words “phreak” and “hack”. The founding editors of the magazine, known by the pseudonyms “Taran King” and “Knight Lightning”, edited most of the first 30 editions. This was the magazine that got CTS into hacking for the first time. She’s now a world renowned hacker and running zellic, a crypto research firm.
Read the latest Phrack 72nd issue.
References:
Wednesday 8/7/2025
Toxic BBQ at Sunset Park, Foxtail Pavilion
Hackers
Phone Phreakers
Radio Frequency Galore
Remember back in the 1970s when Steve Jobs and Steve Wozniak built out blue boxes in order to talk with the Pope in Vatican city from sunny Cupertino? The community now thrives at DEFCON with the ham video village and the radio frequency village. At the Toxic BBQ, the tools and gadgets come out in full force.
Here we have a 10 ft Reception Amplified VHF connected to a ICOM IC-705, which is designed for HF (High frequency), VHF (very high frequency), and UHF (ultra high frequency) bands.
Brief overview of the RF spectrum:
HF (High Frequency)
Range: 3 MHz – 30 MHz
Wavelengths: 100 m – 10 m
Key feature: long-distance communication via ionospheric reflection (“skip”)
VHF (Very High Frequency)
Range: 30 MHz – 300 MHz
Wavelengths: 10 m – 1 m
Key feature: line-of-sight communication, usually up to ~100 miles with repeaters, less without
UHF (Ultra High Frequency)
Range: 300 MHz – 3 GHz
Wavelengths: 1 m – 10 cm
Key feature: Also line-of-sight, but penetrates buildings better than VHF. Shorter range outdoors, but great for urban environments.
Example: 70-cm ham band (~420–450 MHz). Also used in walkie-talkies, Wi-Fi, cell phones, and GPS.
While in Las Vegas, we listened to people in New York, communicating over 14.233 MHz, in the HF range, with the 20-m band, known for long-distance worldwide, communication since signals bouncing off the ionosphere.
To search for other ham radio operators, the community created a site called QRZ, where each operator has a call sign.
For example, the founder of QRZ is Fred LLoyd, with the callsign of AA7BQ. Searching by that on his page yields his personal site
Another community of Ham Radio Operators is Alaska Morning Net . Post your call sign and checkin through the web to tune into the conversation every day.
The last cool product discovered was the Hack RF One by Great Scott Gadgets with the PortaPack by ShareBrained Technologies.
You can use the HackRF One to
Receive and decode ADS-B signals from airplanes to see live aircraft positions.
Simulate aviation transmissions (for testing receivers)
Capture and replay key fob unlock/lock signals (for research into car key security)
Test garage door opener or RF-based keyless entry systems
Transmit Morse code (CW) tones for ham practice or beaconing.
Transmit noise or test interference signals to study how radios behave under jamming
aprs.fi, APRS (Automatic Packet Reporting System) shows live and historical positions, telemetry and messages from APRS stations (ham radio operators, weather stations, balloons, boat, by aggregating packets from the APRS-IS internet backbone and from local receivers
The last resource to get into the radio wave space is RTL-SDR. Here the community posts hacks, tools, and resources to build up the workings of the radio and the internet.
Thursday 8/8/2025
DEFCON vendors, Hak5’s Wifi Pineapple pager and Red Team Tools
What is the Wifi Pineapple Pager?
A pen-testing tool that is able to
impersonate networks
collect networks
collect handshakes
randomize MAC addresses
Spoof DNS and DNS Cache Poison
To interact, modify, and experiment with the Wifi airspace, the pineapple is the tool for the job. It is used to be able to create rouge access points to grab user data and set up enticing phishing websites to trick the enticing user to enter their login credentials
Red team tools are also in the pen-testing framework, instead of operating over the Wifi airspace, these tools are used for physical bypass. Check out redteamtools.com for a burrata salad of exquisite physical bypass tools, door shims, lockpicking kits, hybrid RFID cards. On another note, for software related red-teaming, check out RedTeam-tools, 150+ tools and resources in a github repo.
AI Village with Reality Defender
I had a chance to check out two setups at the AI village, the deep fake bot made by zeetwii and Reality Defender where adversaries setup Google Meet’s, Zoom’s and other video conferencing software with deepfakes like Leonardo Di Caprio or Keanu Reaves. After joining these calls with Reality Defender, they alert you when a deep fake has been spotted.
To create deepfakes, try out these repos below:
Wall of Sheep by the Packet Hacking Village
Image playing 2000’s DOTA at a LAN party while Yousuke Yukimatsu is spinning. That’s what the packet hacking village felt like.
On one of the main side walls, they have a wall of sheep, where cleartext credentials (or other revealing data) is projected on the wall. The goal is to communicate a friendly but blunt lesson about network hygiene—don’t use network services without proper encryption!
Hacker Jeopardy
Hackers drink beer while answering specific questions related to the DEFCON community. Come for the drama, stay for the knowledge~
Besides DEFCON, I learned the largest gatherings of hackers are at the Chaos Communication Congress in Europe, coming December 27th-30th this year, and Hope Conf in NYC, August 15-17th.
Friday 8/9/2025
nRootTag - Exploiting Find My and Transforming Computers Into Unauthorized Trackers by Chapoly1305
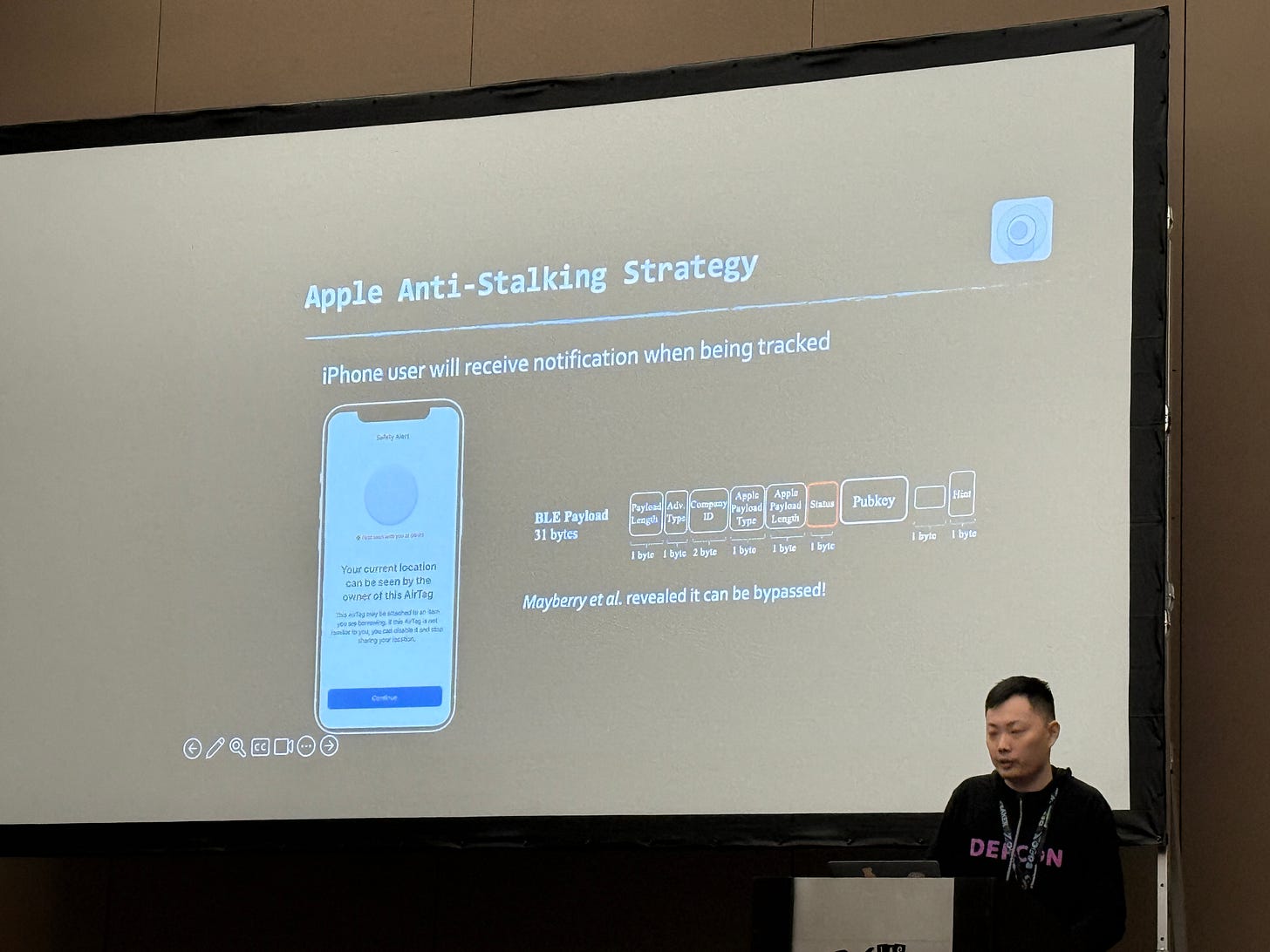
Junming “Chapoly1305” Chen gave a talk about how to exploit the Airtag interface.
The exploit comes down to the BLE (Bluetooth Low Energy) payload that is sent from the Airtag to the iPhone. If you change a bit on the protocol for Find My, and put an AirTag into someone’s bag, the iPhone they carry around won’t let them be noticed by it since the iPhone thinks it’s a Mac and not an AirTag.
Read more on the research here.
Meshtastic Under the Microscope: From Chirps to Chat by Allan Riordan Boll
Meshtastic is an off grid, multi-power, low power mesh network, using a technology called LoRA to transmit the signal a couple of miles, creating a form of decentralized communication. There’s open source firmware and lots of community momentum. Since meshtastic operates on a different radio band, it requires new hardware to be able to run and communicate with others.
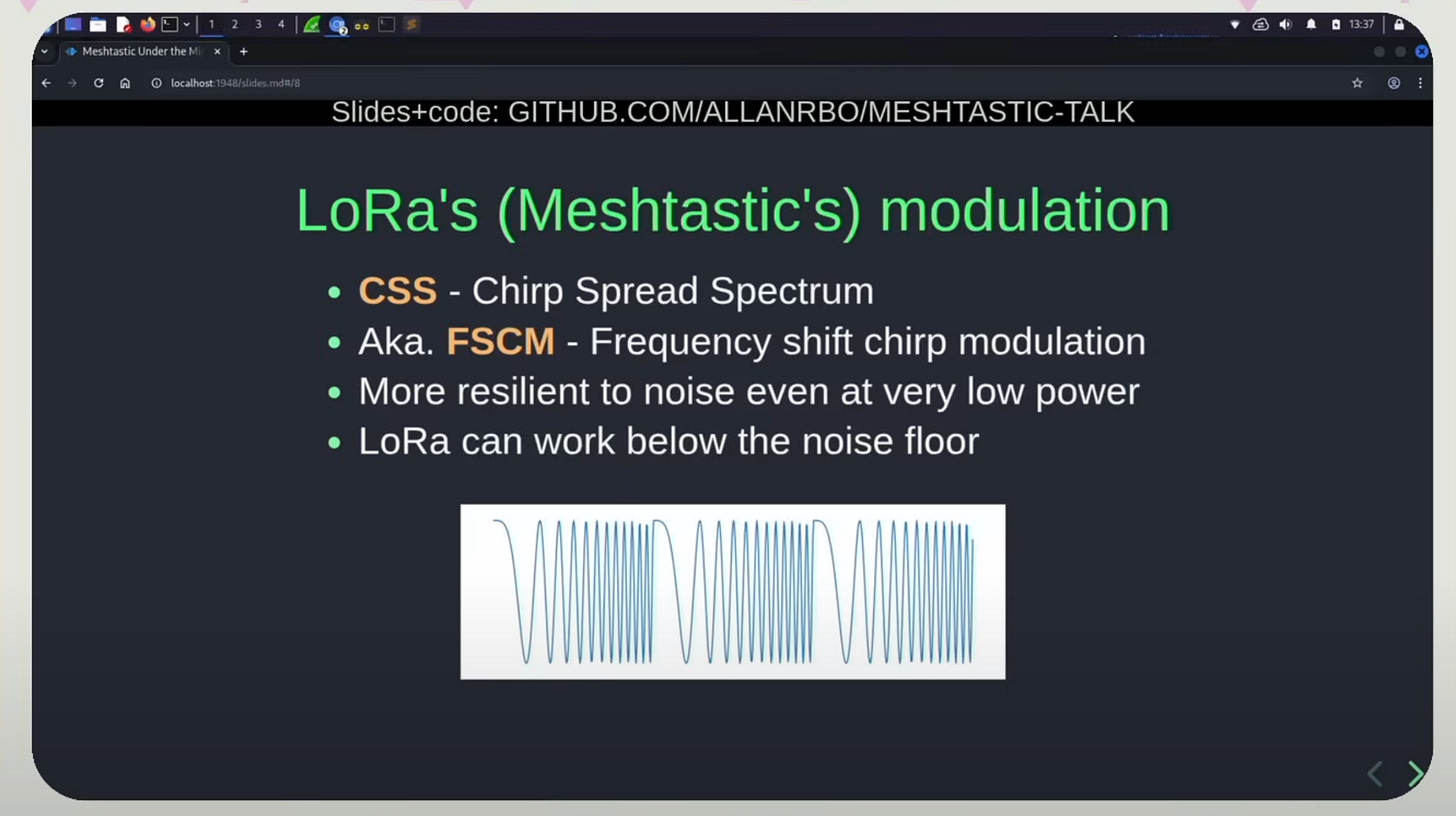
Meshtastic’s signal frequency is CSS (Chirp Spread Spectrum) which is a very specific type of modulation that is very resilient to noise, which makes it work at very low power.
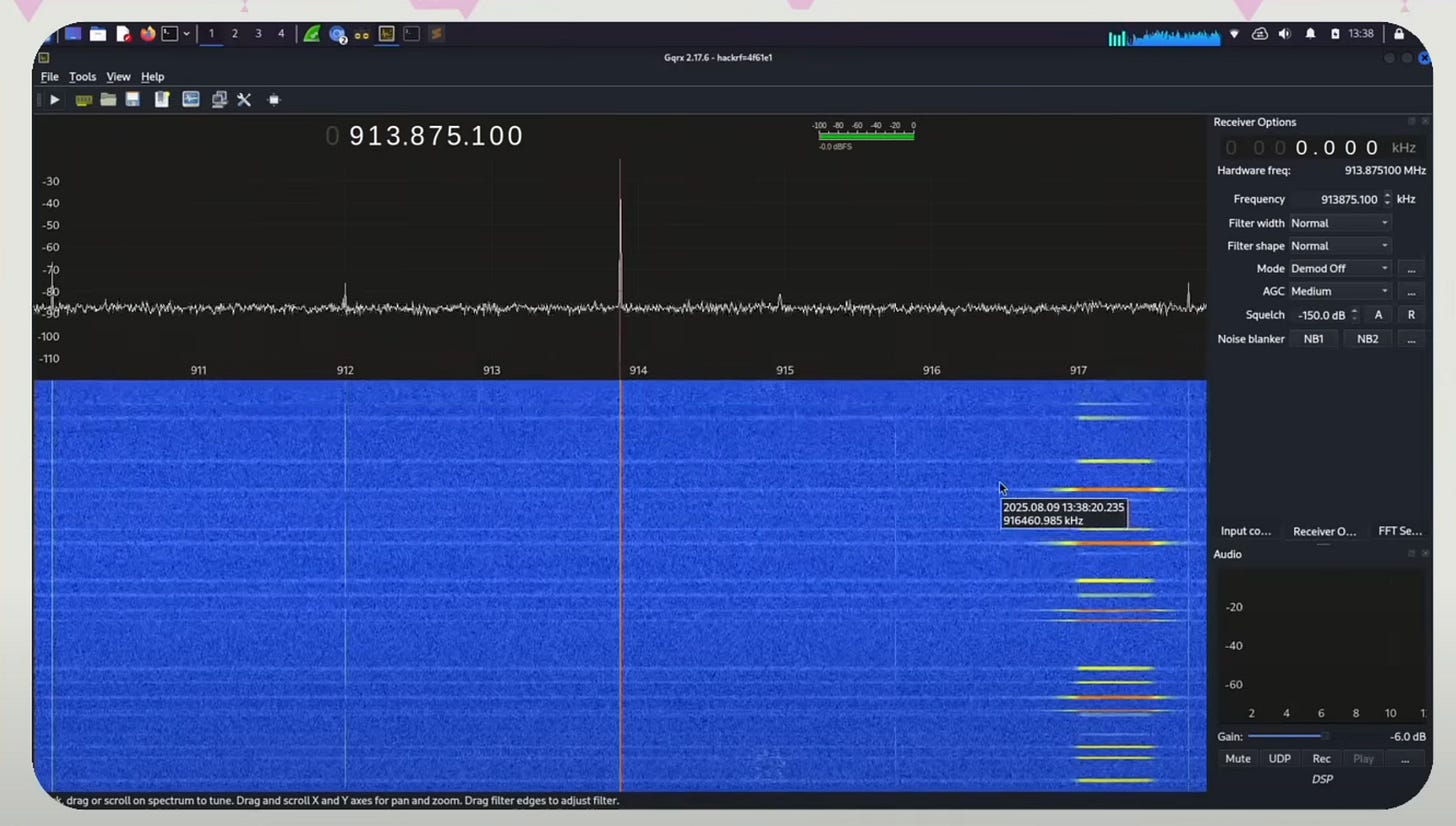
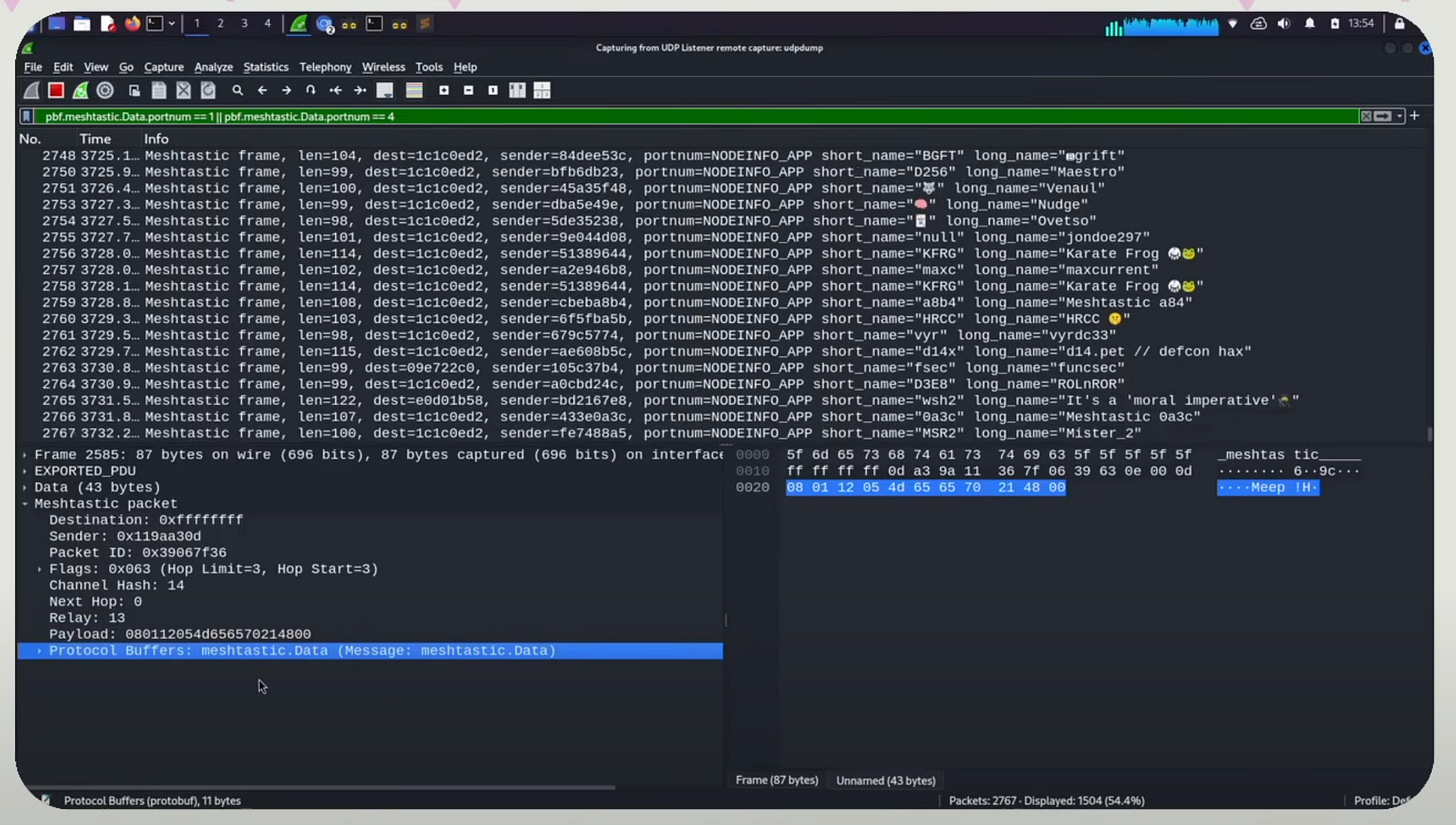
Running the software titled GQRX, which is a software defined radio, we explored, viewed, and recorded radio waves. We see lots of activity around 970 MHz which is the default meshtastic configuration that most people are running at DEFCON.
After using wireshark to decode meshtastic packets, figuring out which bytes of the packet correspond to destination, sender, packet ID, flags, channel hashes and the payload, Allan showed how to write a script to then send packets over the meshtastic protocol so that audience members were able to receive communication! Full script here.
Overall, a great deconstruction of the entirety of meshtastic - from understanding the specific wavelengths for meshtastic, packet decryption using wireshark, and then reconstructing the packet to then send to other meshtastic nodes on the DEFCON ecosystem.
Full talk here:
Compromising Threat Actor Communications by Ben "polygonben" Folland
What are the foundations for malware?
Infostealers
Command and Control
Threat intelligence
Operational Security
Malware Analysis.
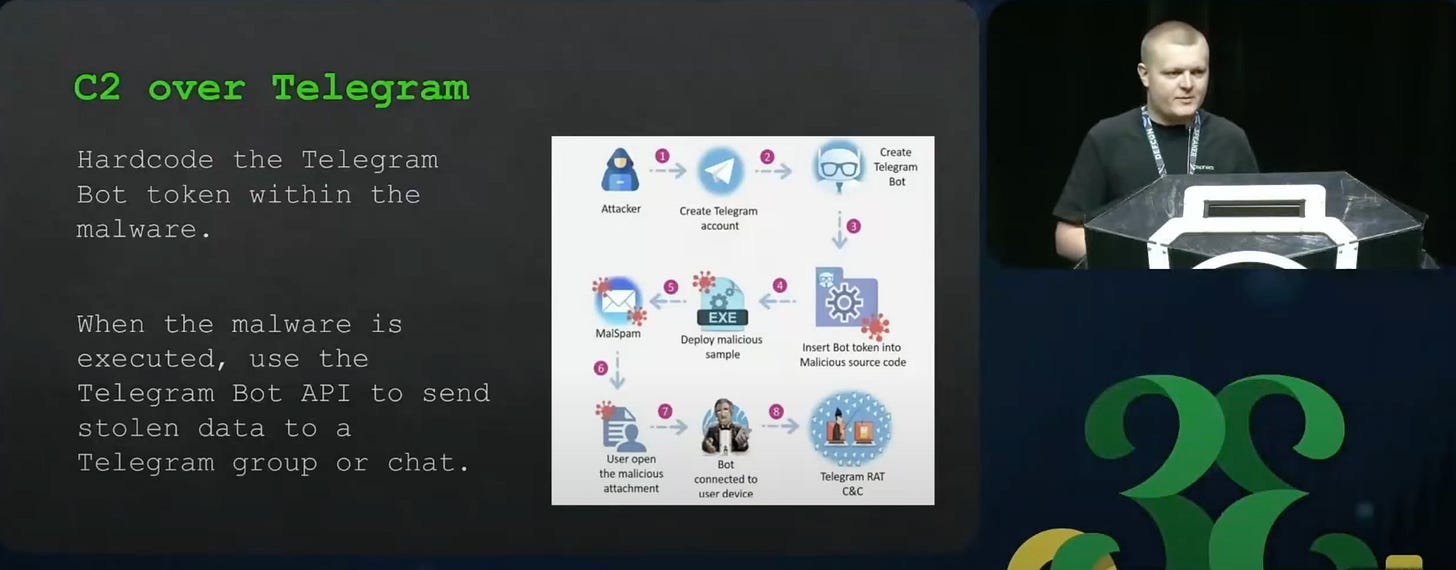
Some of the most common malwares include: Lummastealer, Redline, Vidar, and FormBook. Malware will communicate using a technique called C2, command and control, which allows victim machines to communicate with a threat actor owned location.
As a command and control platform, Telegram is one of the best since it has high-availability, cheap, and “serverless”. By creating an account, getting an API key and setting up a Telegram Bot, you have a quick and easy way to have command and control. Even RATs (remote access trojans) developed by nation states, use telegram as a way to communicate.
Ben was able to find out a malware developer’s telegram API key, intercept their chat message logs, and conduct a thorough investigation of their phishing email stack, VPS servers, and all types of malicious activity they were doing.
Level UP OSINT by Mishaal Khan
Went over to the red team village to learn more about OSINT techniques for practical online investigations and threat hunting.
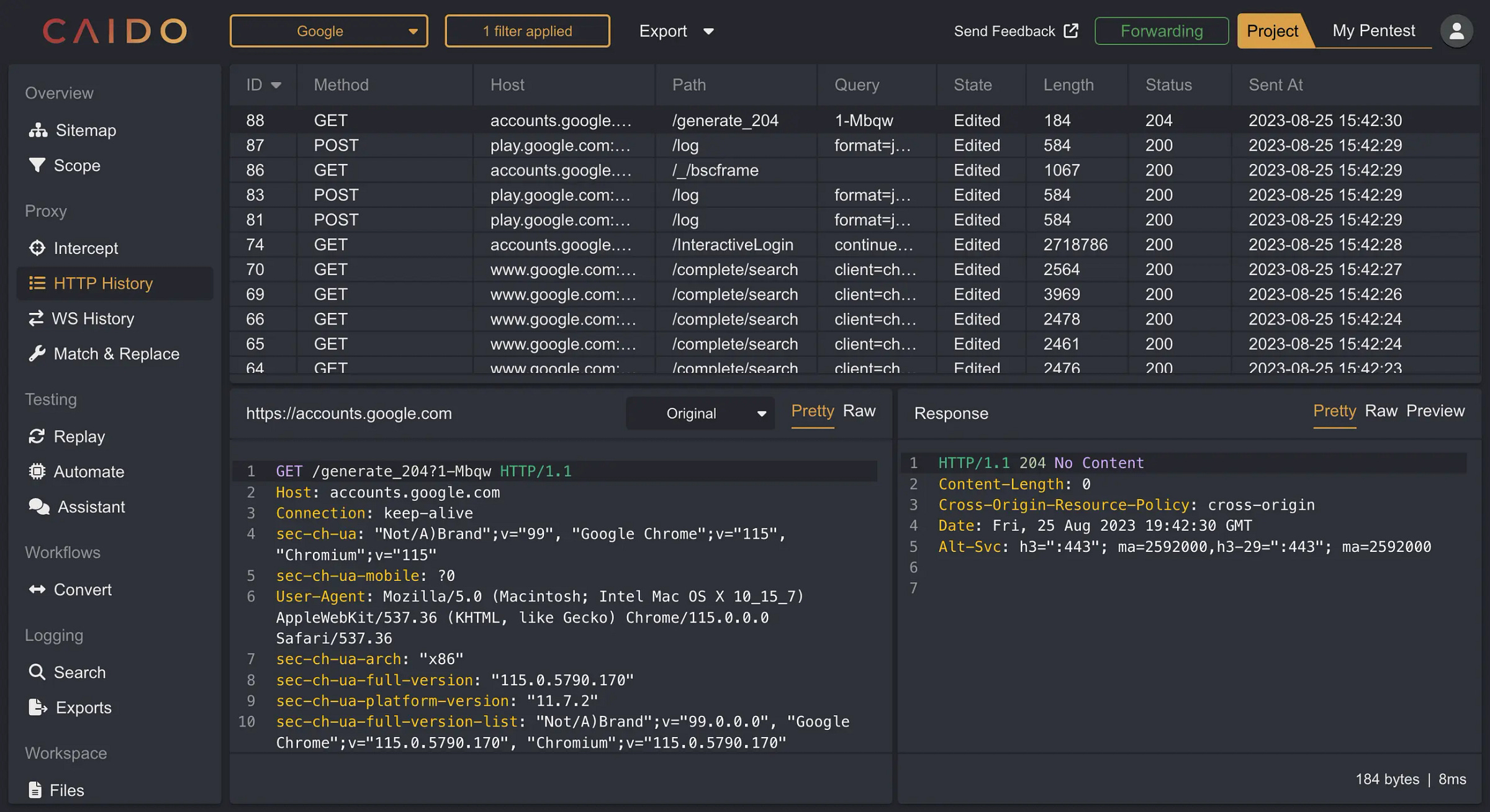
Some of the best tools for doing OSINT include Kali Linux with Burp Suite and Caido. With Caido, you can easily intercept, proxy and view HTTP requests in real-time as you browse while Burp Suite is the industry standard for conducting pentesting for organizations.
Here are a few exercises showcasing the power of OSINT.
Voter Information Lookup
We looked up Dwayne Johnson’s Voter Information Lookup through the state of Florida and we were able to pull out his street address, city, zip code and county name.
The internet never forgets and you can look up any historical data with these sites
Whoxy.com - given a domain name, you can use Whoxy to find out who owns the domain
Archive.org - look up any website
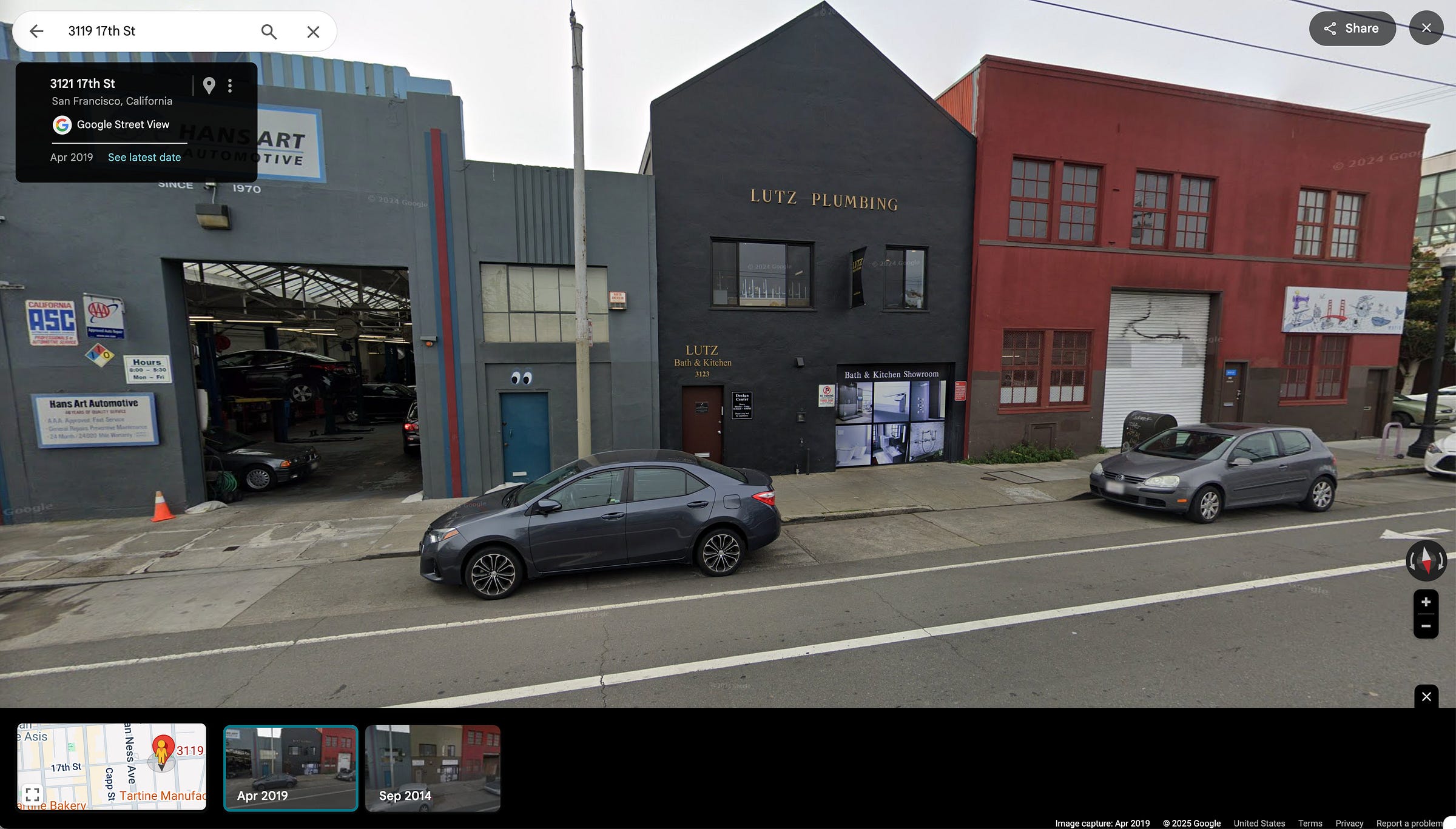
Google Street View - Click into the date and choose from the latest timeline selector on the bottom to be able to see the change between the two dates.
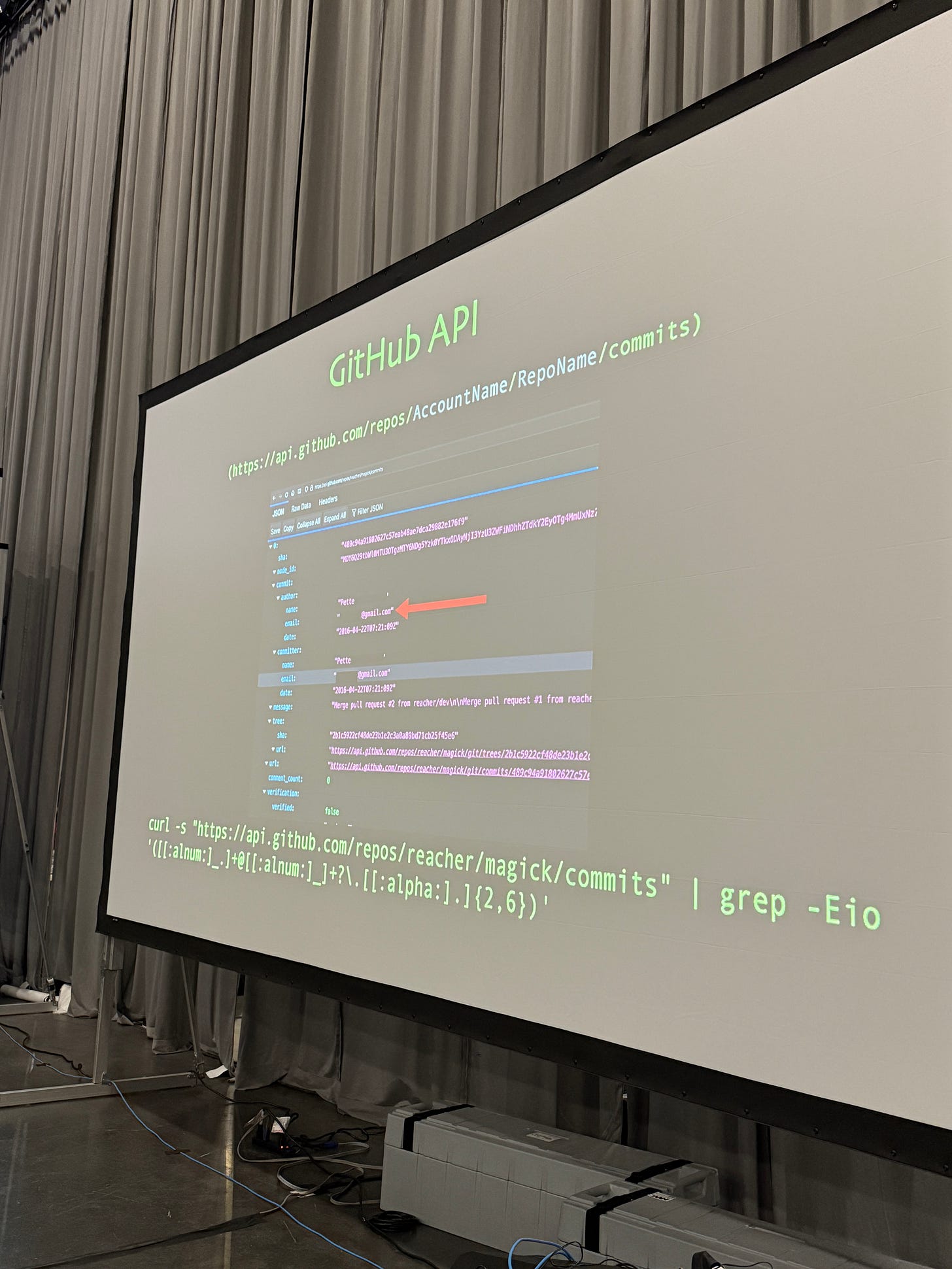
Use the Github API to get the email address of people on Github commits.
Using the curl command,
curl "https://api.github.com/repos/{AccountName}/{RepoName}/commits"and replacing {AccountName} and {RepoName}, we can use regex to extract out specifically the email address from the commit log. Here’s one to extract the user {reacher}’s email from their repo, {magick}. Run it in warp to see it for yourself
curl -s "https://api.github.com/repos/reacher/magick/commits" \
| grep -Eio '([[:alnum:]_.]+@[[:alnum:]_]+\.[[:alpha:].]{2,6})'For those interested in diving into the world of OSINT, here’s a list of resources to dive into the deep end of the pool.
Resources:
Trainings by Mishaal Khaan
Maritime Hacking village
Dropping by the the Maritime village, I played around with the user experience of Simrad Yachting. Similar to drone and flight navigation software, SIMRAD user experience has a map view dashboard with currents and geological topologies, the ability to set headings on the boat, as well as visibility into the current instrumentation of the boat, depth, position, and speed over ground.
Why is the heading selection hanging from the left side of the screen, hugging the compass? It looks awkwardly placed, but I’m sure the designers had a reason to put it there.
For those interested in yachting user experiences, check out
Rolls Royce’s mtu NautIQ bridge, an integrated bridge solution tailored for yachts ranging from 30 to 40 metres in length
Anatomy of a Crypto Scam by Nick “c7five” Percoco and Kitboga
Kitboga got his start because his owne grandma was scammed out of her life savings. Like Dae-su oh in Park Chan Wook’s Oldboy, the feeling of vengeance gnawed at him, and with his successful talent as a voice actor, he made it a point to scam the scammers. A few calls turned into his friends encouraging him to post on Reddit, and with a post on reddit that blew up, he kept on honing his craft and now he’s a 3 million youtube subscriber helping the world by wasting scammer’s time, and entertaining us.
Nick “c7five” Percoco is the CSO of Kraken. He has been in the computer security industry since DEFCON8.
Saturday 8/10/2025
Portswigger Awards: Top 10 web hacking techniques of 2024
Rewards were presented for cutting edge hacking research done including:
Hijacking OAuth flows via Cookie Tossing
ChatGPT Account Takeover Wild Web Cache Deception by H4R3L
OAuth Non-Happy Path to ATO by th0mas.nl
Double Clickjacking: A New Era of UI Redressing by Paulos Yibelo
Exploring the DOMPurify library Bypasses and Fixes by Kevin Gervot (Mizu)
WorstFit: Unveiling Hidden Transformers in Windows ANSI by Orange Tsai
SQL Injection isn’t dead: Smuggling Queries at the Protocol Level by Paul Gerste
Confusion Attacks: Exploiting Hidden Semantic Ambiguity in Apache HTTP Server by Orange Tsai
Congrats to Orange Tsai for winning the top award and also three-peating (three 1st place wins in the last 3 years) for his Confusion Attacks research.
Full list of the Top 10 web hacking techniques
Recap:
DEFCON is the premier conference for hackers. To nerd out on all the low level details from flipper zeros, to meshtastic, OSINT, malware, and more was a sight to behold. Catch you in 2026!
I wrote this piece to share the latest cutting edge of security research, open doors from the security world to the general public, and help crystallize all of my experiences at DEFCON.
If you’re in the hacking space or in the cutting edge of security, I’d love to hear from you.
References:
Hackertracker’s list of all DEFCON 33 talks and events